{{item.title}}
{{item.text}}

{{item.text}}
Managing identity and access management (IAM) – is highly complex and can tax administrative teams. A secure, intuitive and customized user experience is now a prerequisite for business success. Organizations can benefit from IAM that focuses on continuously improving operations – and also enhances service level agreements (SLAs) and cost savings.
We provide an experienced, scalable team to deliver success in your complex environment. Our team can manage the day-to-day operational tasks for IAM services, and maintain the infrastructure with continuous monitoring of the environment's health. We will be involved in developing and sharing metrics to track the IAM program’s posture and be responsible for maintaining the compliance and audit controls for the program.
Effective identity and access management is a business imperative for most organizations today. Increasing regulatory expectations demand transformative responses and enhanced operational processes.
PwC’s IAM service capabilities offer a comprehensive scope of activities that enable your office to focus on strategic initiatives, while simultaneously sourcing the day-to-day operational capabilities.
Identity Access Management (IAM) Operational Services
Privileged Access Management (PAM) Operational Services
Vendor experience
PwC has longstanding relationships with various IAM vendors — including SailPoint, ForgeRock, Okta and CyberArk — winning numerous awards over the years.
Deployment accelerators
Years of deployment experience has facilitated creation of numerous deployment accelerators that reduce ramp-up time.
Resource strength
PwC has experienced IAM resources (750+) available globally to provide 24/7 support.
Flexible resource model
Leverage a flexible and scalable resource pool that best satisfies your operational and oversight needs.
IAM infrastructure maintenance, monitoring and support
Constant monitoring, identification and resolution for critical operational issues
Reporting and dashboards
Implementation validation
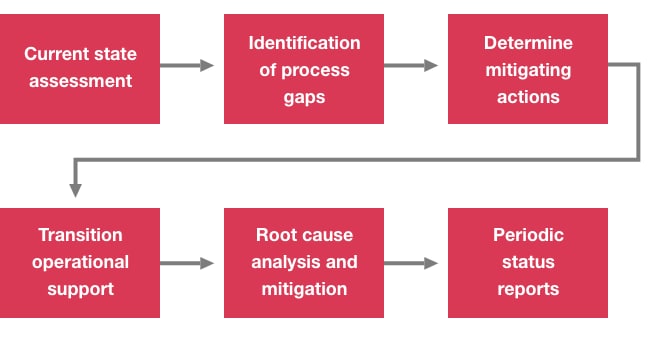
Identification and resolution of process gaps
Standardization across landscapes and environments
As part of IAM managed services, we focus on automating several processes to significantly reduce manual efforts associated with repetitive tasks. As your organization’s IAM capability expands, we look for opportunities to integrate more enterprise tools with the IAM solution and further increase the efficiency of day-to-day operations via automation.
{{item.text}}

{{item.text}}