{{item.title}}
{{item.text}}

{{item.text}}
Companies bidding for defense contracts are estimated to have to comply with Cybersecurity Maturity Model Certification (CMMC) requirements starting in 2025, coinciding with the first phase of the program’s rollout. Prior to then, CMMC may be included in defense contract solicitations as early as December 16, 2024.
In comparison to past regulations, current CMMC requirements represent a streamlined model designed to encourage compliance and accountability.
Affected contractors and subcontractors should begin their compliance planning now, and shore up their ability to defend against ongoing targeting by advanced and persistent threat actors.
Fall of 2024 brought forth a much-anticipated update regarding the CMMC rule for safeguarding Controlled Unclassified Information (CUI). On October 15, 2024, the Department of Defense (DoD) released updates to 32 Code of Federal Regulations (CFR) Part 170, commonly referred to as the CMMC Program final rule. CMMC requires updates to both 48 CFR (Parts 204, 212, 217, and 252) and 32 CFR (Part 170) before it takes effect.
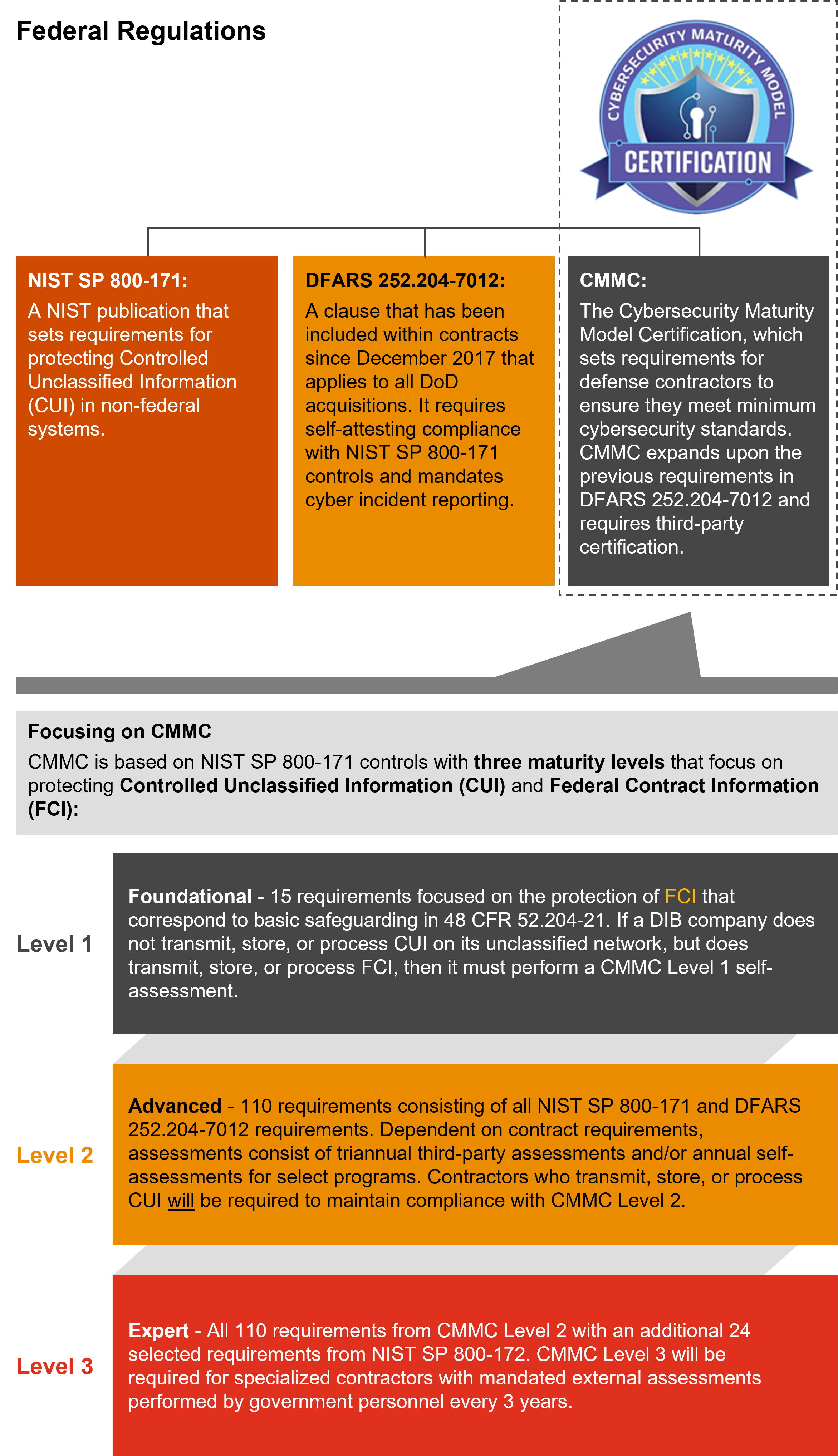
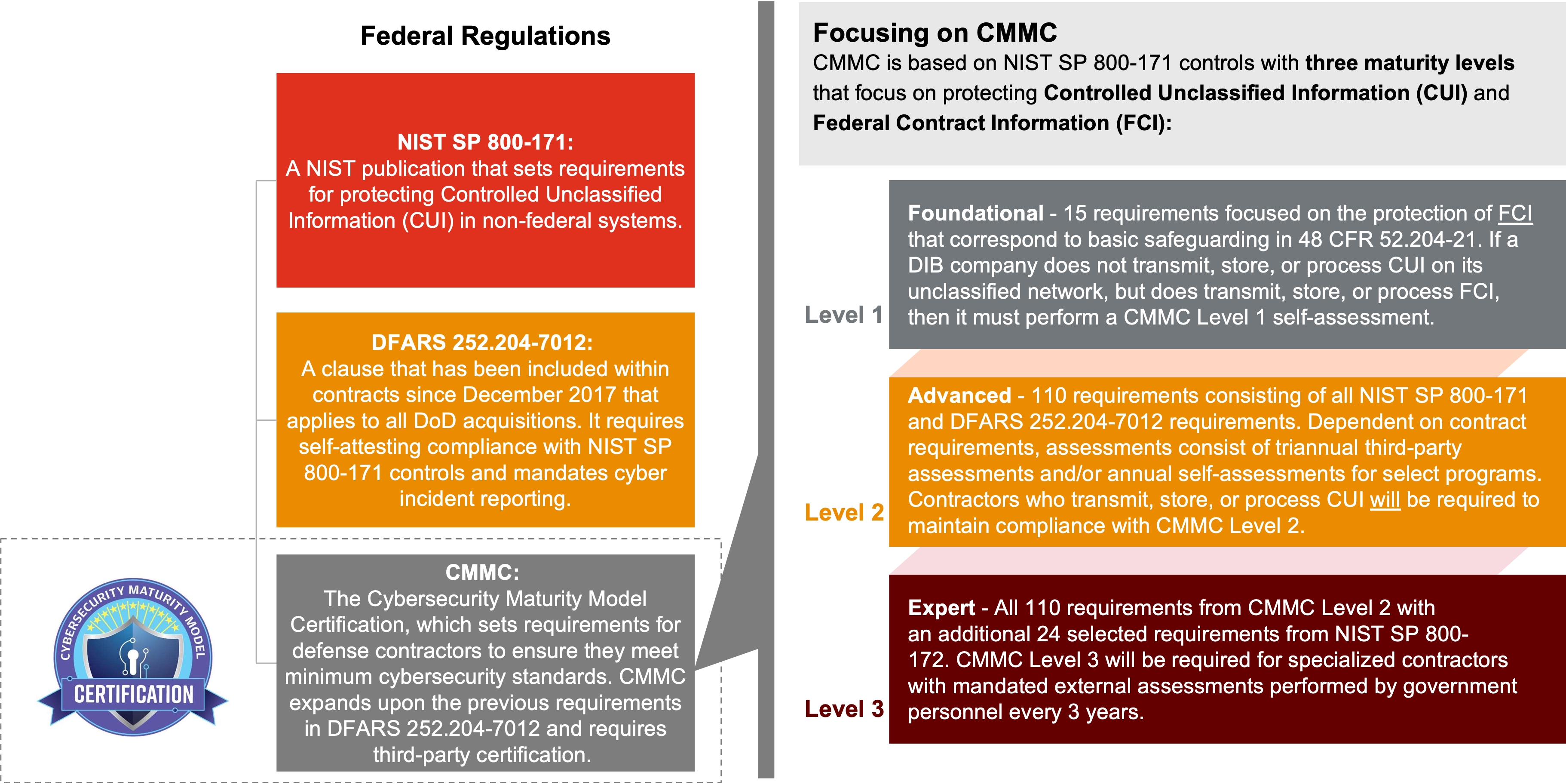
As of the publication of the proposed rule, National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 Revision 2 and portions of NIST SP 800-172 have been referenced as the set of requirements to meet depending on CMMC Level. This is in accordance with an indefinite Class Deviation published which excludes the use of the new NIST SP 800-171 Revision 3 for CMMC for now. It is expected that Revision 3 will be required at a later date after the CMMC program has been rolled out and shows general adoption. Included were a number of key updates to the prior proposed rule.
Key Updates:
In 2020, the DoD introduced the Cybersecurity Maturity Model Certification (CMMC) process, designed to bolster security, safeguard sensitive unclassified information, and enhance visibility into the defense supply chain.
The CMMC mandates standards, practices, and processes that all companies within the DoD supply chain—not just the defense industrial base (DIB)—must implement to bid on defense contracts. What’s at stake is big: The DoD’s budget request related to two key acquisition appropriations totaled $313 billion for FY2025.
Defense contractors are often the target of frequent, persistent, and complex cyber-attacks. A recent joint agency report from the Federal Bureau of Investigation (FBI) shows that advanced cyber actors have been responsible for espionage, sabotage and reputational harm against DoD targets and other critical infrastructure since at least 2020. Targets included entities connected to US government services, financial services, transportation systems, energy, and healthcare sectors.
Complying with CMMC can be a significant endeavor, one that could impact as many as 220,000 (Source: CMMC Program Final Rule, Background) primary contractors and subcontractors, large and small. In addition to DIB companies, CMMC affects a mix of traditional and nontraditional industries, such as higher education (research and development), health services, retail, critical infrastructure providers (including telecom), and technology (including cloud service providers).
The CMMC Program rule has been finalized in the Federal Register as of October 15, 2024. Phased rollout of the CMMC Program starts 60 days after the publication of the final Title 48 CFR CMMC acquisition rule.
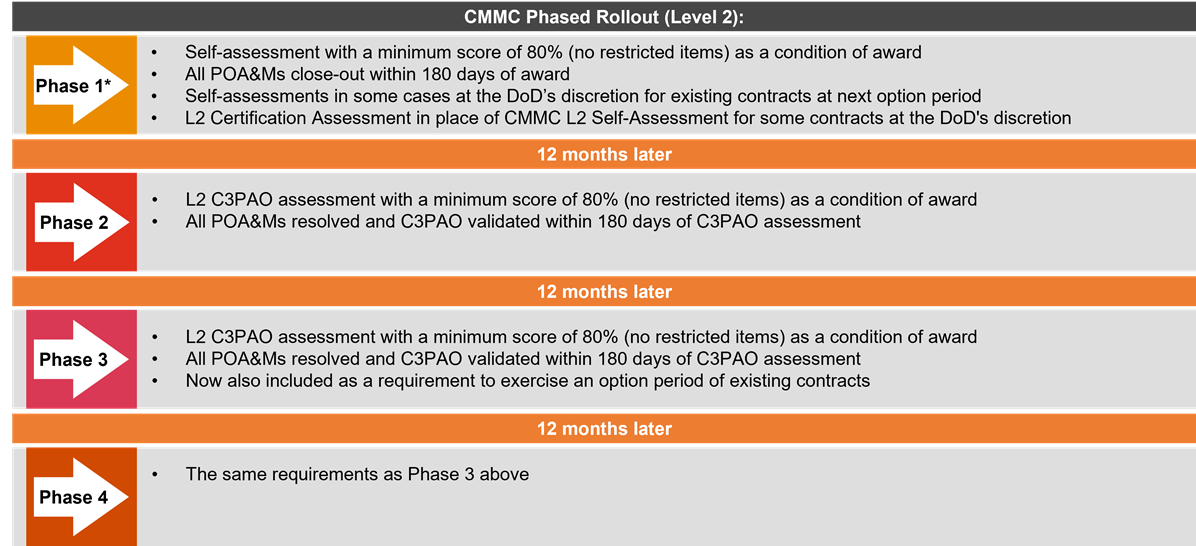
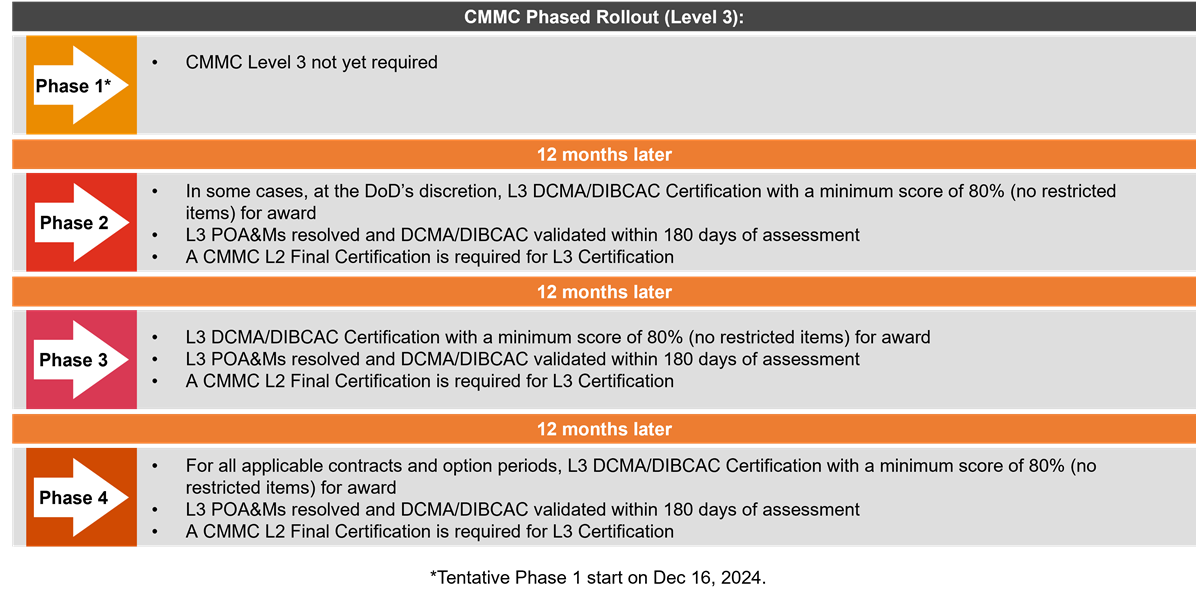
Source: Office of the Under Secretary of Defense, Acquisition & Sustainment
As updates to the CMMC Program final rule were published in the Federal Register as of October 2024, the phased rollout of CMMC is imminent. It is estimated that some contractors and subcontractors can expect to start seeing CMMC requirements within their DoD contract solicitations towards the beginning of 2025. Coinciding with the finalization date of the program rule, CMMC may be included in defense contract solicitations as early as December 16, 2024, at the DoD’s discretion.
The complexities of CMMC compliance will likely require quick action, a disciplined response, and deep knowledge of DoD acquisition rules. Meeting all requirements prior to third-party assessments includes significantly more effort than self-assessments in the past.
To start the process towards CMMC compliance, contractors should first evaluate the environment for compliance (documentation, control effectiveness, resources) and continue to expand their documentation and readiness.
{{item.text}}

{{item.text}}