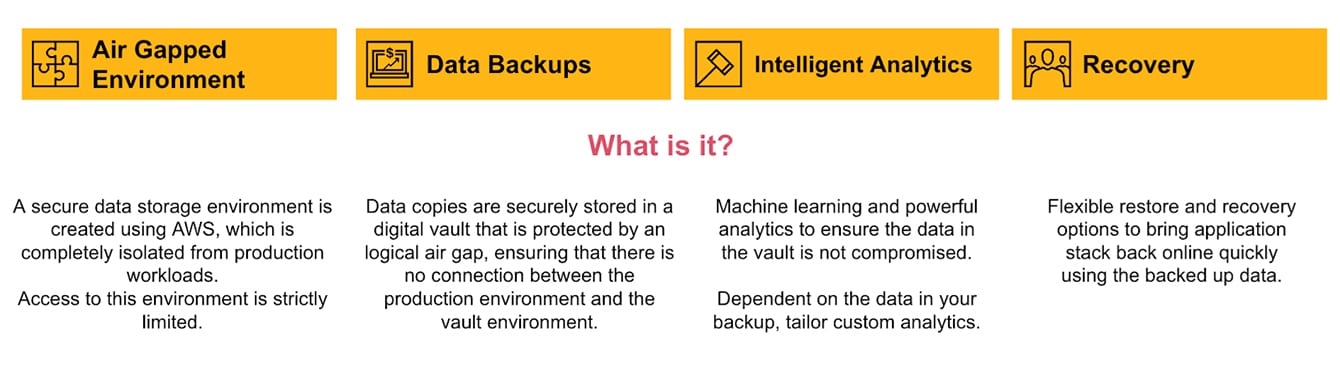
{{item.title}}
{{item.text}}

{{item.text}}
“Creating an immutable copy of backup data in an air-gapped network location is now a must for any data protection strategy.”
Fintan Quinn,Gartner, How to Recover from a Ransomware Attack Using Modern Backup Infrastructure, June 4, 2021Cyber resilience is the ability of an organization to continuously deliver the intended outcome despite adverse cyber events. It has an overlap with disaster recovery where both cyber resilience and disaster recovery involve plans and actions to restore normal operations after an incident. Cyber resilience includes disaster recovery as part of its broader strategy.
There are multiple key themes when it comes to designing for cyber resilience:
Protect: Proactive measures taken to safeguard systems, networks, and data.
Prepare: Activities to ensure an organization can effectively respond to and recover from a cyber incident.
Recover: Actions taken to restore systems, networks, and data to their normal state after a cyber incident.
While working with clients on the topic of cyber resilience, it’s important to define a few things upfront, so that the design can be tailored specifically to the attributes such as:
Recovery point objective (RPO) - In a cyber recovery scenario, RPO designates the variable amount of data that will be lost and unacceptably impedes the flow of normal business operations.
Recovery time objective (RTO) - In a cyber recovery scenario, RTO designates the amount of time that can pass before the disruption begins to seriously impede the flow of normal business operations.
Crown jewel applications - The portfolio of applications that will require to be recovered in a cyber recovery scenario.
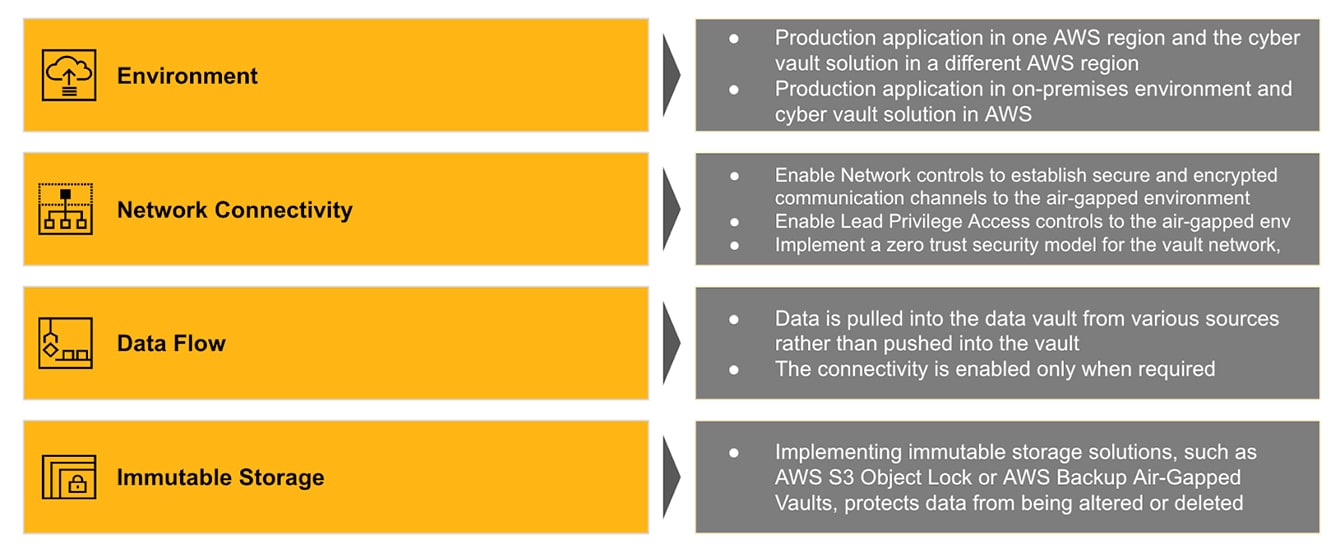
Topic 1: How do we deploy an environment that’s air-gapped from the primary network? Common considerations are as follows:
Topic 2: How many copies of data do you keep to make sure it’s safeguarded and how do you confirm your vault data is not compromised?
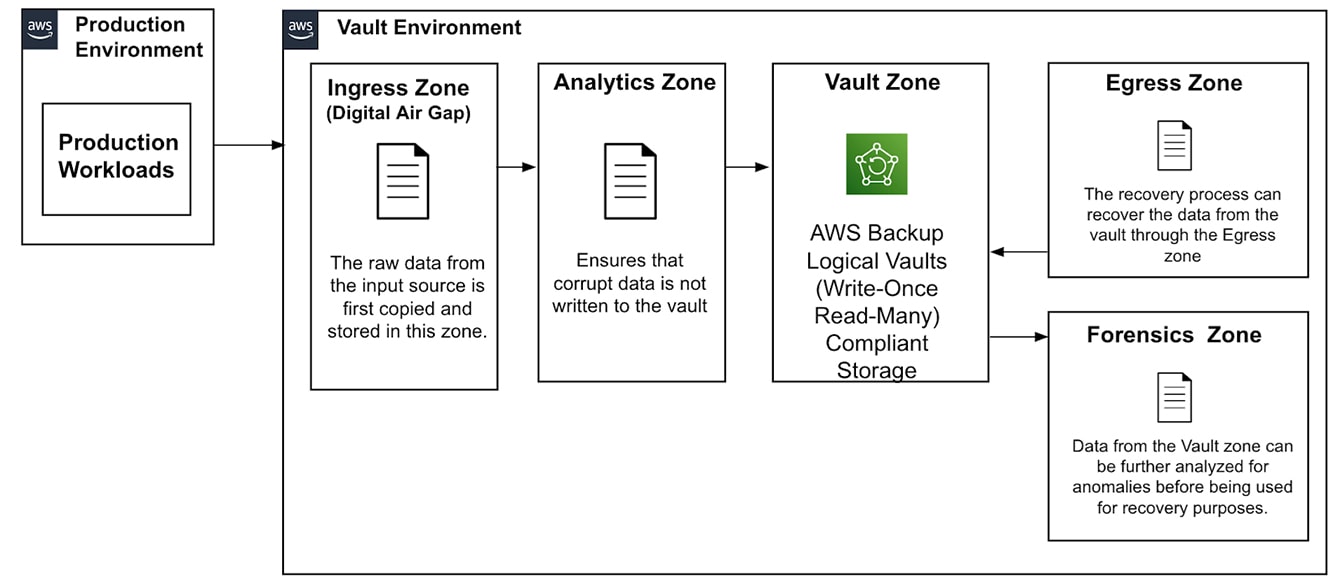
The raw data from the input source is initially copied and stored in the ingress zone.
In the analytics zone, this data undergoes analysis to confirm that no corrupt data is transferred to the cyber vault.
Once confirmed to be error-free, the data is stored in write-once read-many (WORM) compliant storage, which prevents any modifications after writing. This ensures the data remains secure and can be safely used during a ransomware incident.
In such an event, data from the vault zone can be further examined for anomalies before being utilized for recovery.
The recovery process retrieves data from the vault through the egress zone. By maintaining separate ingress and egress zones, we safeguard the vault from external access, confirming that only authorized services can access the data.
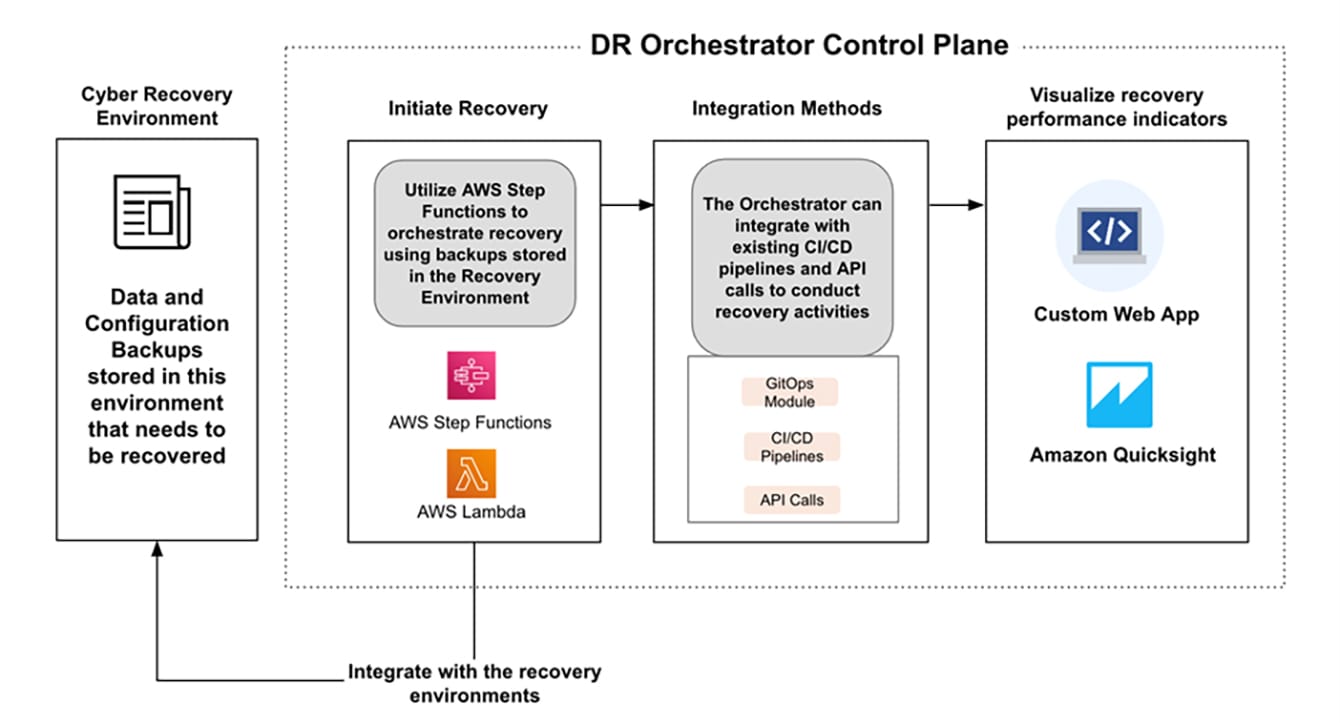
Topic 3: How do you recover your environment from the configurations and data stored in the vault?
One of the most effective ways to recover from a cyber attack is to have a reliable and fast backup process. It often involves restoring to a previous point-in-time just before the attack occurred.
PwC has developed the disaster recovery orchestrator framework on AWS to enable resiliency across an organization’s foundational AWS environment and application services, reducing the dependency on various supporting teams required to conduct regular disaster recovery testing. The disaster recovery framework is a customizable solution that can automate the failover of critical services to a healthy AWS region in the event of an incident and the failback of AWS services to their original state.
This framework can be used to orchestrate the failover activities in a disaster scenario by making API calls into the vault zone and creating an environment from the latest backups.
For modernizing resiliency and response, we often help clients address questions such as:
What are the core challenges with designing for cyber resilience in the cloud?
How do organizations handle and respond to outages and disruption in services from a cyber event?
If you would like help in addressing these questions or want to explore any of the focus areas listed above, reach out to us.
{{item.text}}

{{item.text}}