{{item.title}}
{{item.text}}

{{item.text}}
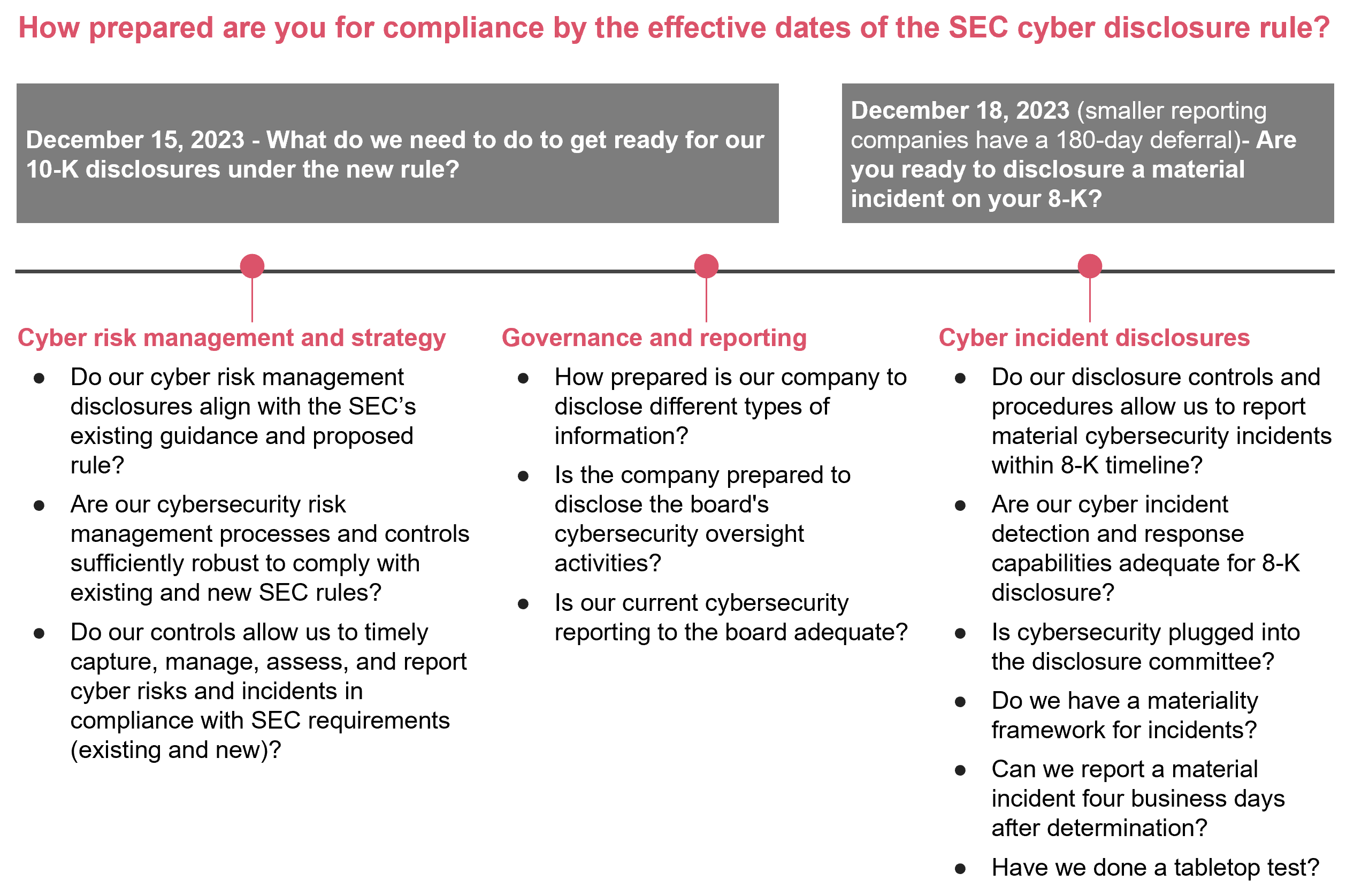
The SEC released its final rule on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure on July 26, 2023.
With this new rule, the SEC puts the onus on companies to give investors current, consistent and “decision-useful” information about how they manage their cyber risks. The final rule requires that, in annual 10-K filings, all SEC registrants reporting under the Securities Exchange Act of 1934 describe the processes, if any, for assessing, identifying and managing material risks from cybersecurity threats. It also requires reporting on management’s role in assessing and managing those risks and the board of directors’ oversight of risks from cybersecurity threats.
It also establishes a defined timeline that requires disclosure of material cybersecurity incidents in Form 8-K within four business days of determining that an incident is material.
With a short time frame for compliance, boards and audit committees will turn to the internal audit function for an independent view on whether their company’s cyber risk mitigation strategies and programs are robust and fit for purpose, as well as to ascertain organizational readiness to comply with the new disclosure requirements.
IA acting as a strategic advisor to the business has never been more pivotal as boards seek to gain assurance over organizations’ cyber posture and to provide consistent and “decision useful” information to investors.
Many companies are not ready today to reveal information about their processes for assessing, identifying and managing material risks from cyber threats to the extent that the new rule requires. Management will likely want to reevaluate the processes underlying the required disclosures now that information will be publicly communicated to investors.
With a narrow window to achieve compliance, IA’s engagement needs to be agile and fast-tracked.
Internal audit can provide an independent assessment of your company’s readiness to respond to the SEC cyber disclosure rules by following these three steps:
Cyber risk has historically ranked high and has been an area of concern in internal audit risk assessments over the past decade. As such, it’s likely that your audit plan has evaluated some of these areas with a close nexus to the new reporting requirements. Given the short ramp-up time, though, an independent and holistic evaluation may be necessary to assess readiness both from a first- and second-line perspective. Here are a few topics worth considering:
The new cyber disclosure rule requires even greater communication and connections among IT and security, finance, general counsel and ERM teams. Internal audit should coordinate with the cross-functional team as it does the assessments.
Coordination with SOX teams can also yield collaborative results. With the evolution of cyber risks, areas of common cyber exposure relative to financial reporting have caused auditors to scrutinize the potential impact of cyber risks on the financial statements more closely. Examples of such areas of common exposure include patch management, intrusion detection, backup and restoration of data, vendor management and wire processing.
Each component of the SEC rule will require cyber capabilities and controls to be demonstrably in place for management to provide investor-grade information in 10-K and 8-K disclosures.
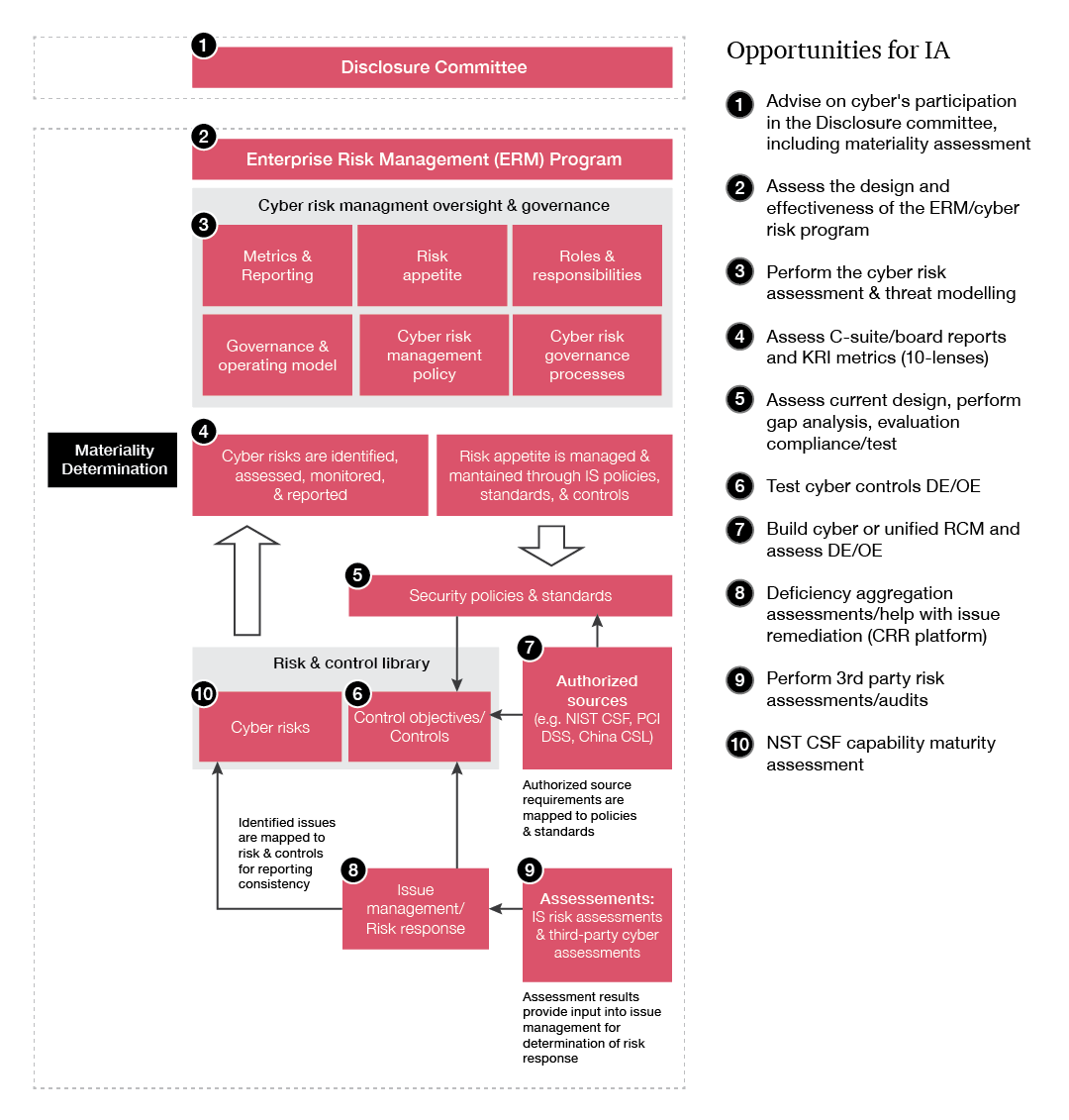
The graphic below illustrates a full view of the interrelated areas where your management team might need to make changes or establish new procedures to comply with the SEC cyber disclosure rule. Internal audit can anticipate where it might provide strategic insights, both in an advisory or in an assurance capacity. Chief audit executives can right-size their engagement for the size of the company, its current cyber program maturity and ongoing work in this area.
Understanding materiality considerations is an area that IA should cover. Materiality assessments are top of mind for all organizations and the process for the assessment — including who is responsible for the ultimate determination — needs to be confirmed in every company. An important requirement for making materiality judgments is contemporaneous documentation of facts surrounding a cyber incident. IA should understand how management plans to conduct contemporaneous documentation and form an independent view of the sufficiency of the documentation.
A second area that IA should consider is participating in tabletops. IA’s independent perspectives and lessons learned through tabletop exercises can be valuable to enhancing stakeholder collaboration and processes.
Organizations that don’t comply with the new rule may face serious consequences, as recent SEC enforcement actions suggest. The commission has levied large fines against companies for not disclosing breaches sufficiently or in a timely manner. Enforcement has focused on two areas — first, that organizations have appropriate disclosures under the requirements, and second, that they have controls and procedures in place to escalate necessary items for determination of whether disclosures are required.
When integrated with the multifunctional team that’s working on the company’s compliance with the new SEC rule, internal audit can serve as an independent advisor — through oversight across all aspects of the disclosure requirements and the various stakeholder groups — to confirm preparedness and response.
{{item.text}}

{{item.text}}