By John Southworth, PwC Threat Intelligence
Threat actors routinely target a variety of web server technologies with the purposes of either gaining initial access to an organisation, or maintaining persistent access to its network. While dropping webshells is a very popular method of achieving either of these objectives, Windows IIS servers offer a different approach via the use of custom modules.
IIS (short for Internet Information Services) is a Windows web server technology that has been around since 1995, that can support multiple protocols like HTTP and FTP, and has millions of devices running it globally. Custom modules can be created for IIS, either as managed modules (.NET), or native modules (C++).1
Seminal work by ESET in 2021 detailed the threat landscape of native IIS backdoors,2 and there has been a variety of research released into IIS backdoors; both in terms of understanding how threat actors are using them,3 and releasing public proof-of-concept IIS backdoors, such as IIS-Raid.4 For instance, PwC researchers have previously presented on the BlackMould IIS backdoor,5 a native IIS webshell initially disclosed by Microsoft.6
A challenge that the PwC Threat Intelligence team found when analysing malicious IIS modules was that standard reverse engineering tools by default do not support the analysis of native modules; making it hard to identify relevant functions or understand the capability of the module itself. As such, we have released a plugin for IDA Pro to help facilitate native IIS module analysis at multiple stages; including:
- Loading in relevant classes/symbolic constants;
- Identifying and renaming the virtual methods of IIS classes;
- Applying function prototypes to the known implemented virtual methods; and,
- Attempting initial retyping of variables in these methods.
The plugin we developed is available on the PwC Threat intelligence GitHub page: https://github.com/PwCUK-CTO/iis-helper-plugin
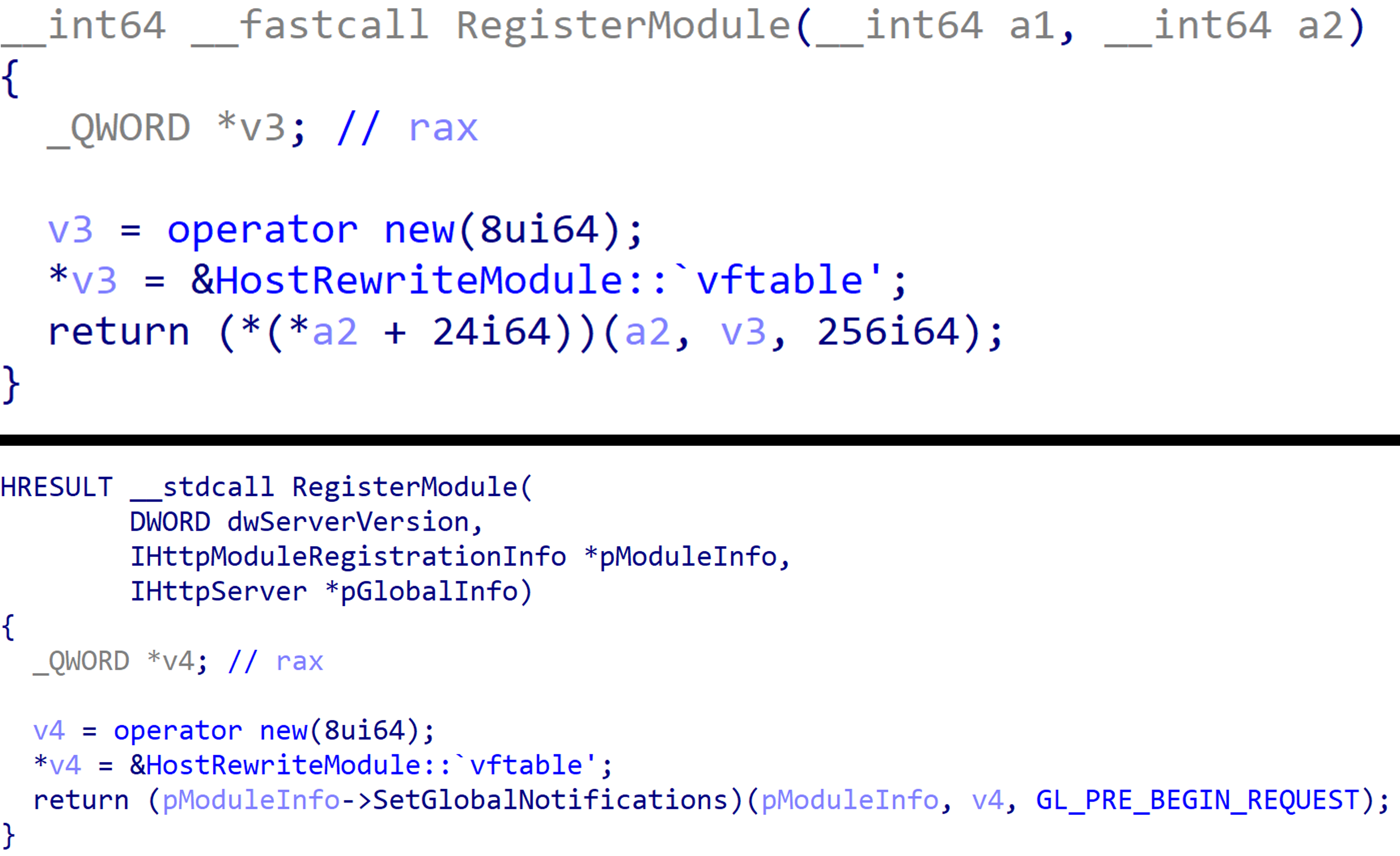
Retyping a function with the IIS Helper plugin
Case study: SessionsIIS
As a case study from our threat hunting, we present a passive IIS backdoor that we uncovered earlier in 2023, which we have named SessionsIIS:
Filename |
isalg.dll |
SHA-256 |
577ca702d73f2090ce583c5b1fbfcb3101d3c79722c98b3aa8dc6598296182f4 |
File type |
Win32 DLL |
File size |
294,912 bytes |
Compilation timestamp |
2022-08-10 15:30:32 |
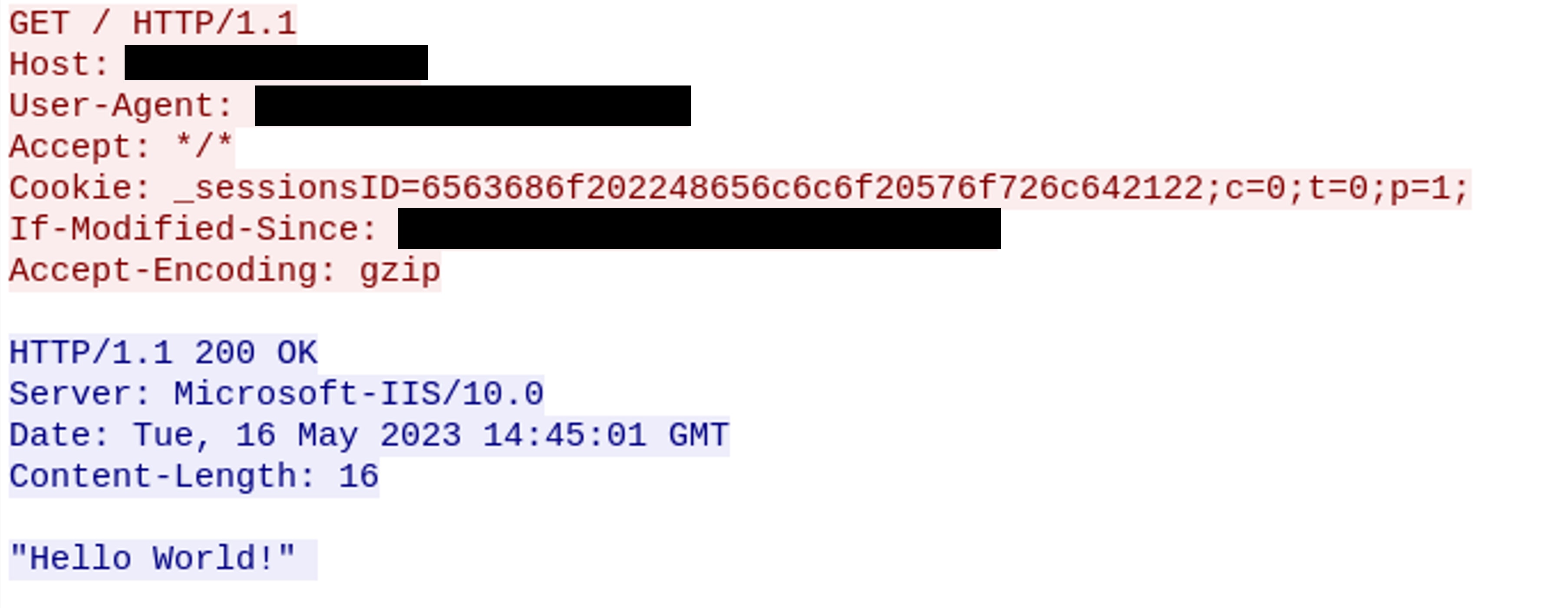
This backdoor, which was likely used to target a government organisation in South Asia, will wait for HTTP requests to be made to the IIS server, and use a fixed “key” in a date field to authenticate requests. If successful, the backdoor will read in hex-encoded commands in a HTTP request, specifically Cookie field in the _sessionsID parameter, which will then be executed on the server. Requests to the backdoor can be chunked using the c and t parameters, and the p parameter is used to execute the commands in a few different ways (such as via popen, or CreateProcessA).
An example HTTP request to SessionsIIS, running a command to print "Hello World!"
Using the IIS Helper IDA Pro plugin on this sample enables quicker identification of relevant functions to analyse, and provides an analyst with all the relevant class information to retype variables to understand how the backdoor works.
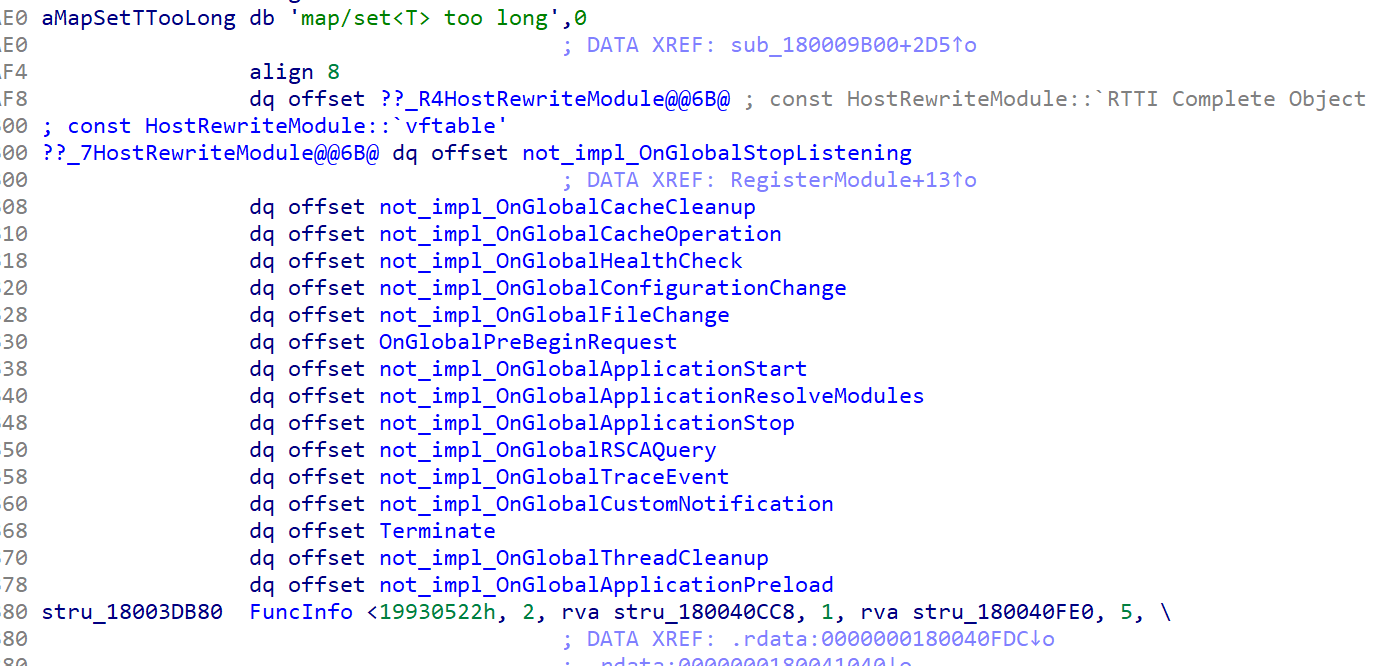
Methods renamed by the IDA Pro plugin
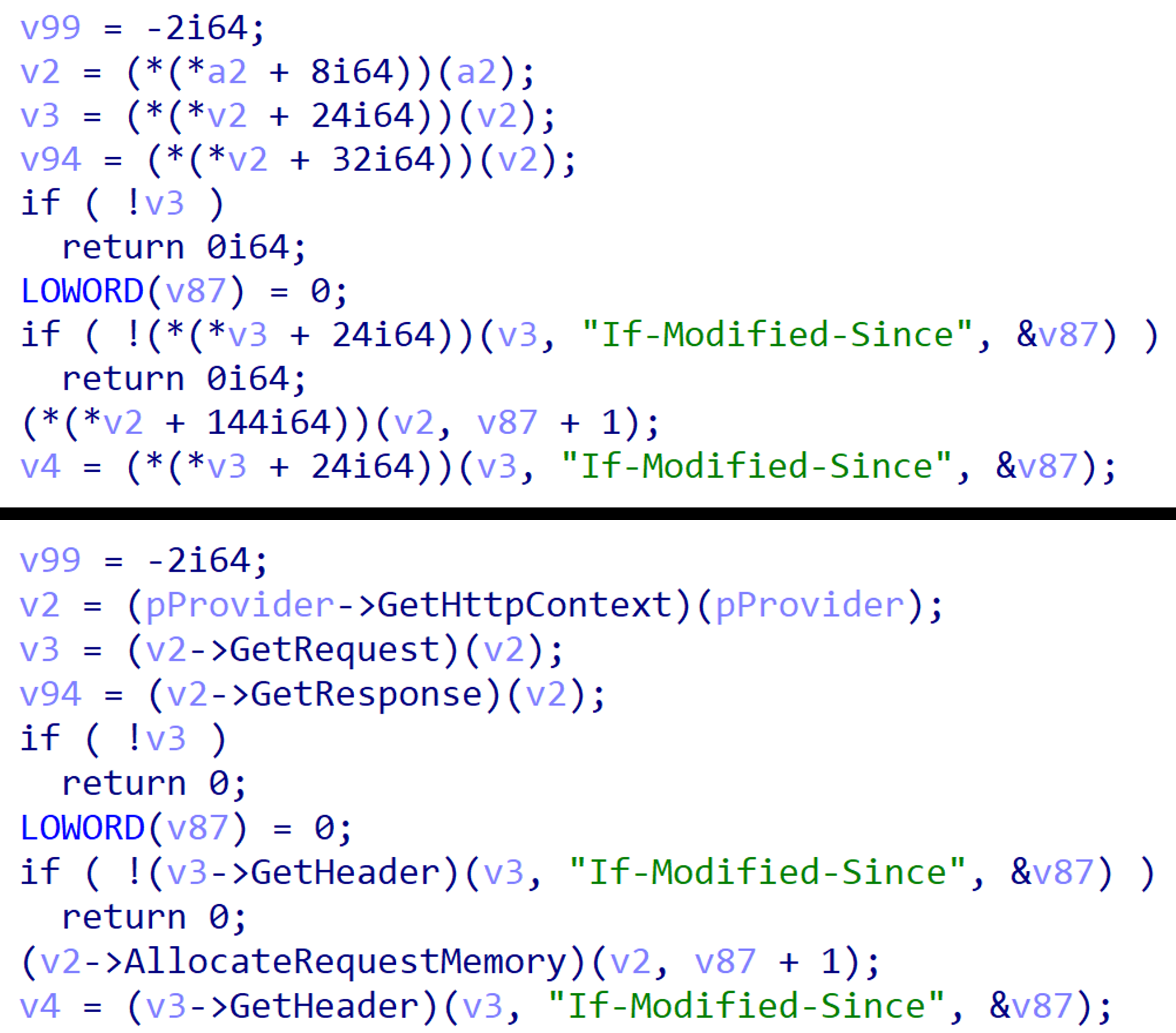
Comparison of the automatically retyped malicious method of SessionsIIS
You can use the following YARA rule to hunt for this backdoor:
import "pe"
rule SessionsIIS_Backdoor_A : Heuristic_and_General
{
meta:
description = "Detects the SessionsIIS backdoor, based on a unique combination of strings"
TLP = "WHITE"
author = "PwC Threat Intelligence"
copyright = "Copyright PwCIL 2023 (C)"
license = "Apache License, Version 2.0"
created_date = "2023-05-15"
modified_date = "2023-05-15"
revision = "0"
hash = "577ca702d73f2090ce583c5b1fbfcb3101d3c79722c98b3aa8dc6598296182f4"
strings:
$ = "_sessionsID"
$ = "If-Modified-Since"
condition:
pe.exports("RegisterModule") and all of them
}
Conclusion
Threat actors will continue experimenting with native IIS modules to maintain persistent access to Windows servers. We recommend that organisations maintaining IIS servers often check for newly registered modules (e.g. via the use of appcmd.exe), or look for suspicious modifications of installed IIS modules.
1 https://learn.microsoft.com/en-us/iis/get-started/introduction-to-iis/iis-modules-overview
2 https://www.welivesecurity.com/2021/08/06/anatomy-native-iis-malware/
3 https://www.microsoft.com/en-us/security/blog/2022/07/26/malicious-iis-extensions-quietly-open-persistent-backdoors-into-servers/
4 https://github.com/0x09AL/IIS-Raid
5 https://troopers.de/downloads/troopers22/TR22_TinkerTelcoSoldierSpy.pdf
6 https://www.microsoft.com/en-us/security/blog/2019/12/12/gallium-targeting-global-telecom/
Contact us

Cyber Threat Operations Lead Partner, PwC United Kingdom
Tel: +44 (0)7725 707360













