We will help you achieve new digitalisation goals
Digitization services

Technology is being constantly built, changed and upgraded but its benefits bring with them concerns about the pace, governmental or industrial regulation, and potential threats. These are all obstacles but there are also opportunities so we offer technology to work for your company. PwC's team of specialists offers a wide range of services and solutions to address any challenges your company may face: from information technology audits to strategy, management, and cybersecurity transformation, to data analytics for your future needs.
Key services
- Information and communication technology (ICT) compliance and audits
- IT strategy and optimization
- Digitization and digital transformation
- Pentest
- Data discovery and structuring
- Source code analysis
Information and communication technology (ICT) compliance and audits
Today, information systems (IS) play the main role in ensuring the operation of the critical infrastructure for business and government. In the era of digitalisation, using critical IT systems for information storage, processing and transmission complicates their protection, especially given the global trend with growing numbers of information attacks that cause significant losses of funds, property and reputation. To efficiently protect against cyberattacks, companies need an objective assessment of their IS security level – it is for these purposes that we encourage you to use our security evaluation and audit services.
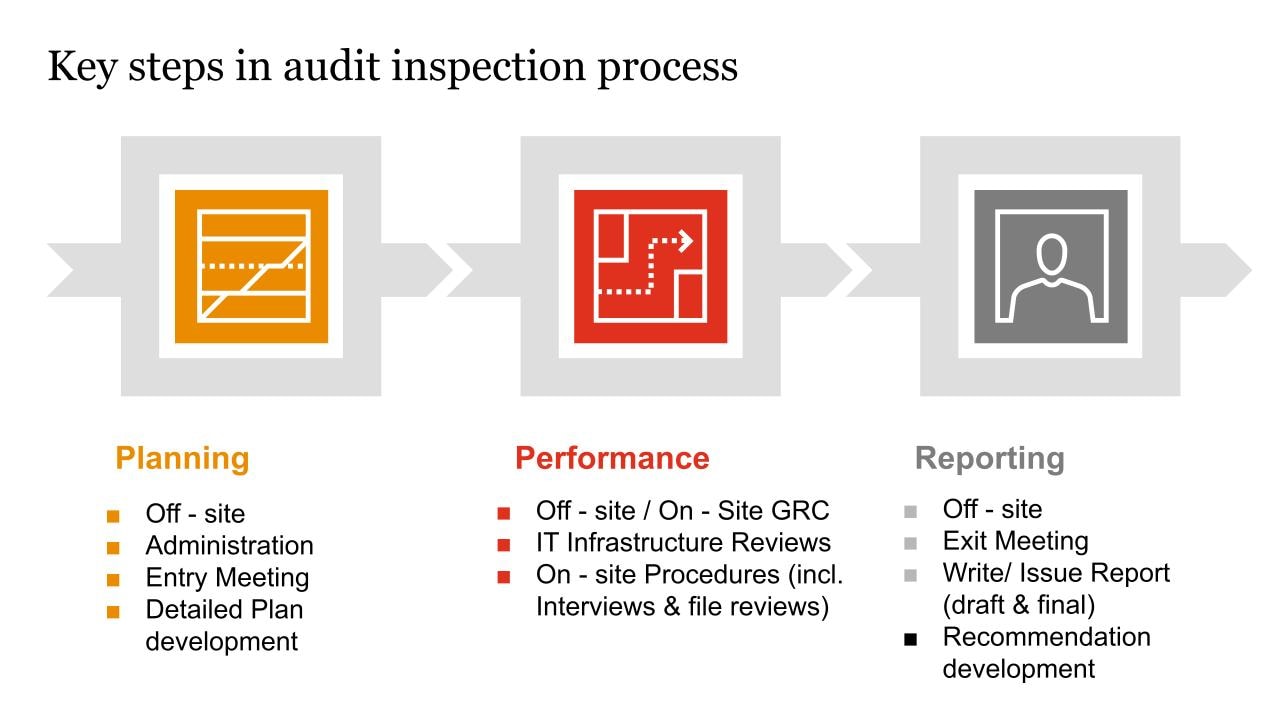
Evaluate your cybersecurity capabilities using PwC’s security analysis service:
- IT security documentation analysis for regulatory compliance
- User access and rights analysis
- End user workstations analysis
- Network equipment and IT security systems analysis
- Threat identification
- Data processing and information leakage analysis
- Analysis of attacker’s behaviour during attack
- Network security check using vulnerability scanners and a pentest (an authorised cyberattack simulation)
- Preparing and improving your IT security documentation
- Devising a plan for final reporting and eliminating weaknesses.
IT strategy and optimization
Successful companies must make tough choices about how to use technology and where to focus their IT investments. With so many options in cloud computing, cybersecurity, specialised software, and other specific operational services, as well as emerging technologies like machine learning and blockchain, a successful strategy is essential to create and sustain long-term value.
The strategy of successful companies is based on a sustainable IT infrastructure, technological growth of the internal organization and ability to adapt to change to achieve common goals.
Solutions offered by PwC:
- Methodology implementation
- IT compatibility
- Future enterprise architecture
- IT efficiency
- Cloud-based solutions
- Shared Services Centre strategy
- Option analysis
Digitization and digital transformation
Making the right digital investments can be hard. But by setting clear outcomes and specific performance metrics, we provide strategic advice, as well as testing and controls (from the design phase onward), to help digital rollouts stay on or get ahead of plan and budget. We help our clients align all digital solutions with business goals, and we carefully manage change among employees. Only well-executed IT investments ensure safe implementation of business objectives, as they correspond with existing organisational processes.
Solutions offered by PwC:
- Holistic IT transformation
- Digital project management
- Usability testing
- Market research
- Development of implementation roadmap
- Management of changes
Pentest
Cybercriminals are rapidly evolving and using increasingly newer and more efficient technologies (ML and AI) in creating threats. Hackers can be outside or inside your company (often employed by it for years). It may well be that your company’s information resources are being tested and hacked, as autonomous viruses can carry out such unauthorised actions constantly. How cybersecure is your IT infrastructure? How can you proactively identify potential threats before they materialise? How can you avoid losing reputation in the eyes of customers? PwC ITS pentest team can help answer all these questions.
We test the cybersecurity of infrastructure and apps with a focus on identifying and exploiting vulnerabilities inherent in business critical IT infrastructure and apps (internal and external):
- Comprehensive infrastructure pentest
- Security checks of Web, Cloud, Mobile and other external resources
- Pentest using Black, White or Grey Box principles
- Drawing up recommendations to mitigate known security vulnerabilities
- Cybersecurity team’s response efficiency assessment
- Source code analysis (dynamic or static)
- Your company’s digital identity threat assessment (OSINT).
Data discovery and structuring
With most of today’s work being done remotely, companies often use cloud platforms where file sharing and storage is the norm. This is a challenge for companies needing to know exactly where their sensitive or regulatory data is located and what kind of data it is (structured or unstructured). We also need to understand who is working with this data and who is accessing it, and whether your company needs this data, with more questions that are sometimes even impossible to answer.
Given the mutual compatibility of today’s business processes, data is held across multiple systems, apps, databases and shared files, making their protection, authentication and confidentiality a challenge for companies. Data discovery, classification and efficient management are a range of services designed to fully identify corporate data and ensure appropriate controls are in place to implement best security practice and regulatory compliance measures. This also helps companies choose more efficiently the right systems for data protection and avoid future data leakage incidents and unauthorised access incidents.
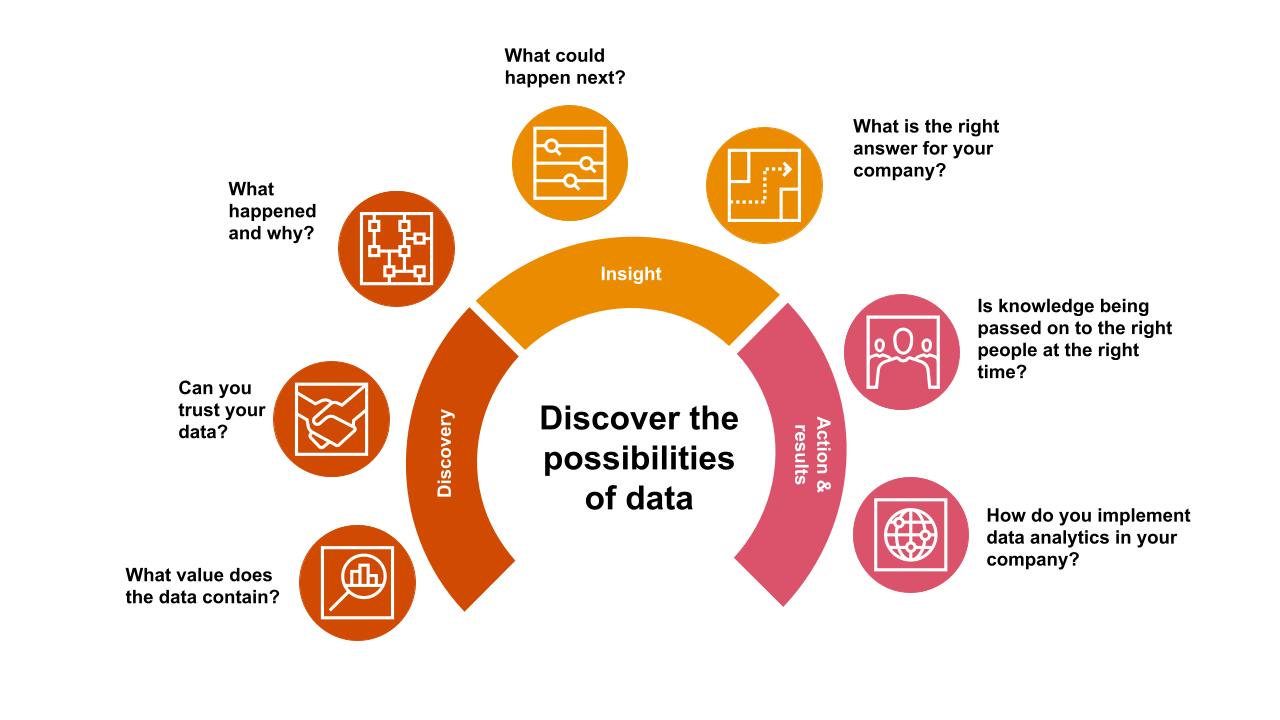
PwC ITS data discovery and structuring experts will help you answer all these questions:
- What value does data carry?
- Can you trust your data?
- What happened and why?
- What could happen next?
- Is knowledge transferred to the right people at the right time?
- What are your company’s data analytics processes?
Source code analysis
According to market researchers, 90% of vulnerabilities exist in app source codes deeply buried in the developers’ workstations and not accessible to most security tools and tests.
Unfortunately most companies do not subject their app source codes to security checks and analysis, which causes dangerous security gaps in the stages between the new app development stage and their full-fledged launch in a production environment.
PwC ITS cybersecurity experts will carry out an in-depth analysis of your app codes to detect security vulnerabilities in:
- Input validation logic
- Memory management
- Authentication
- API integrity and applicability etc.
Contact us







